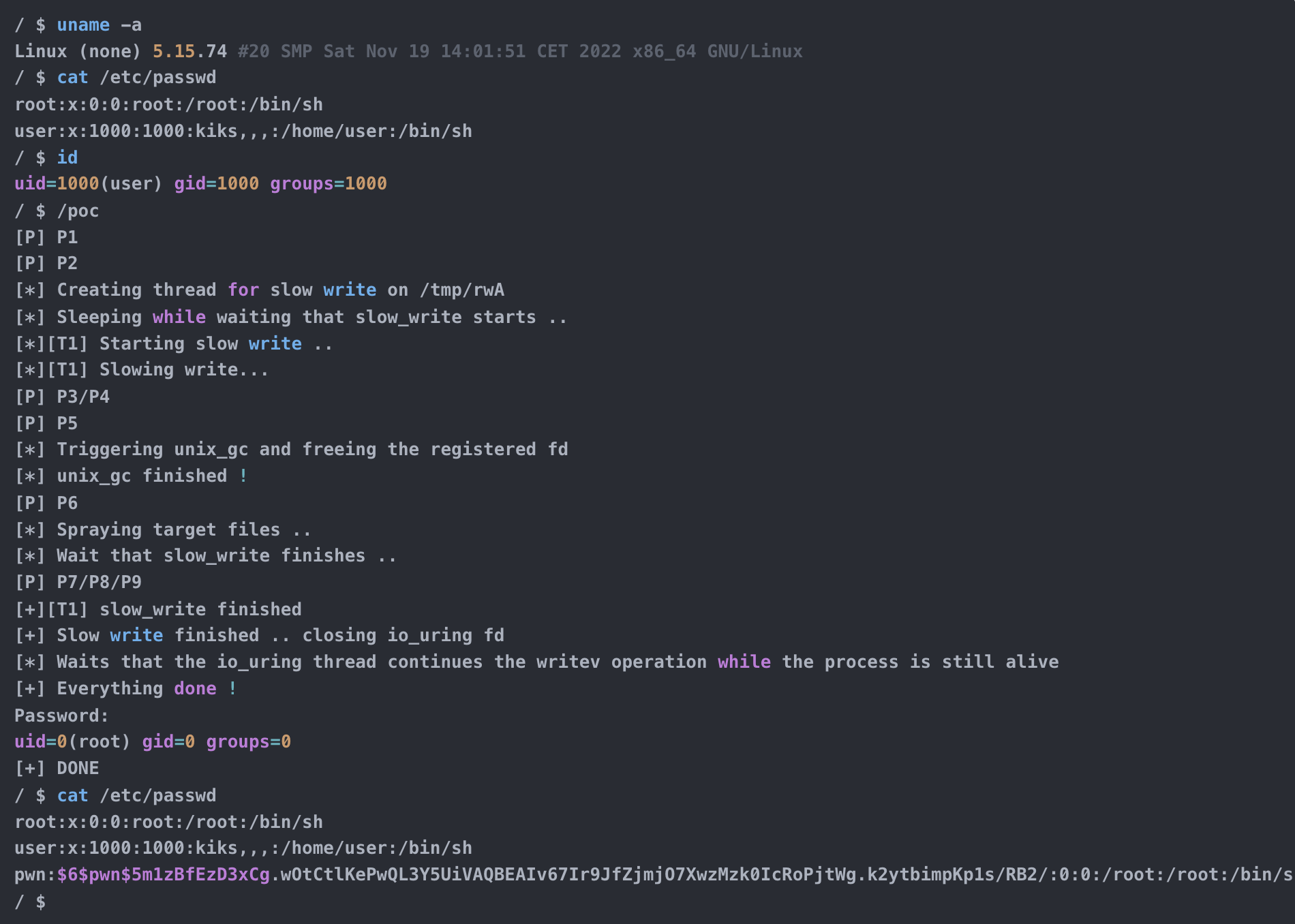
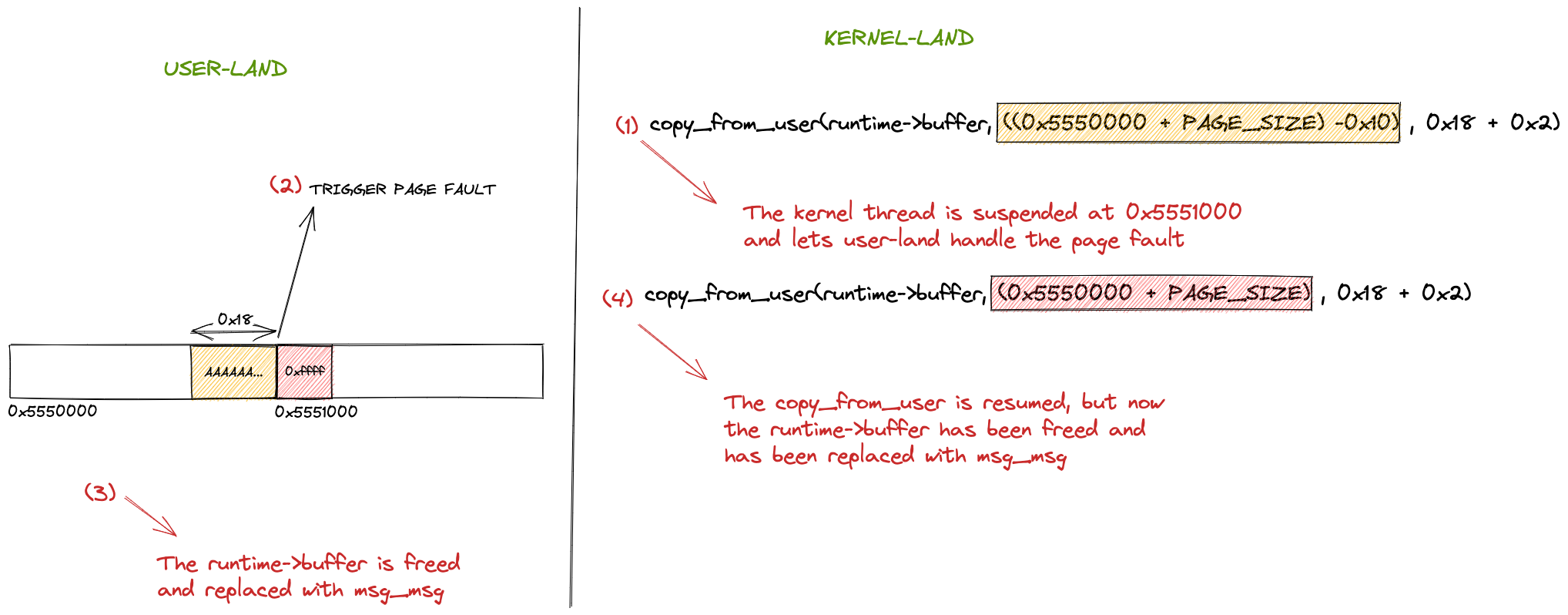
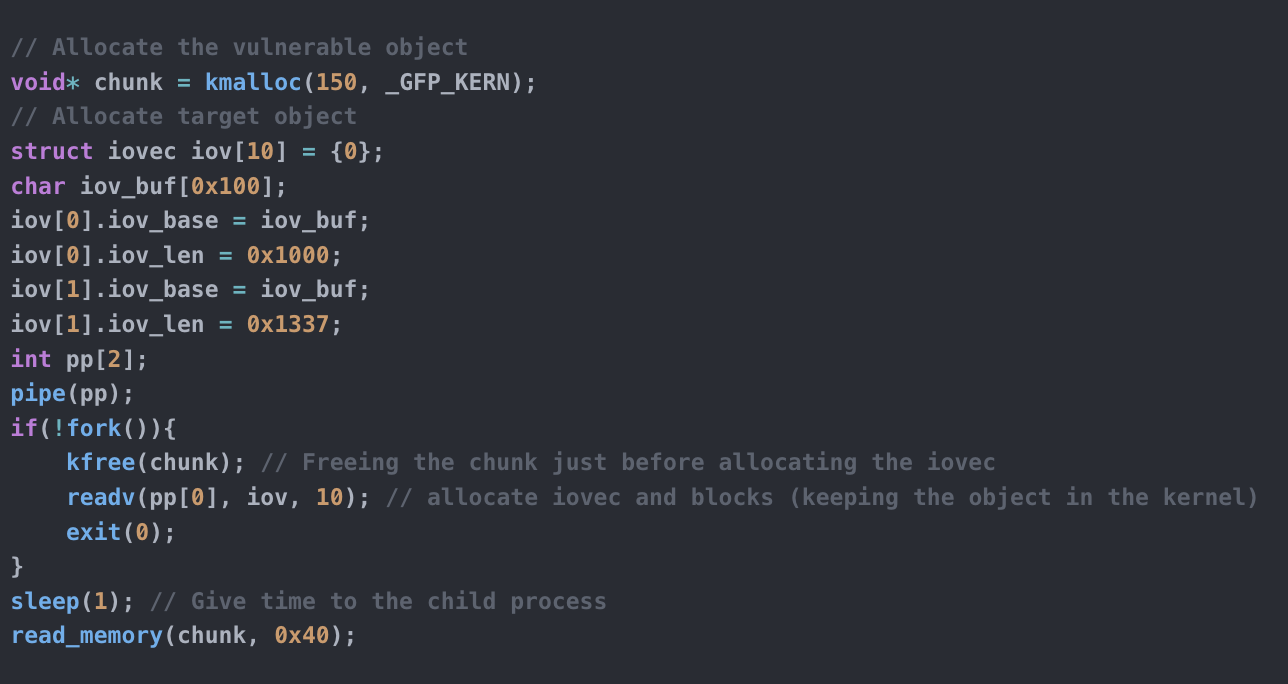
Introduction In the past few weeks, I worked with @LukeGix (checkout his blog post on the same vulnerability here) to exploit the CVE-2022-2602, a very interesting bug from multiple perspectives without a public exploit, that impacts the io_uring subsystem with an Use-After-Free vulnerability handling registered file descriptors.We used a Data-Only attack against kernel version 5.15.74 […]
A few months ago me and my friend Jacopo Tediosi made an interesting discovery about an Akamai misconfiguration that allowed us to earn more than 46,000 dollars. Our research highlighted how manipulating a particular HTTP header made it possible to change the way how proxies communicated with each other and how this allowed us to […]
Slide: https://hacktivesecurity-my.sharepoint.com/:b:/p/alessandro/EX9sSrCCRIlLqvkHoRl7_jQBB6xKgV_qLL9UA5fIwf2Cbw?e=cCQpixMateriale utilizzato nel video (per poter replicare i lab): https://hacktivesecurity-my.sharepoint.com/:u:/p/alessandro/EX08cV3wTzZJsEeEQwZvw80BbybF2CpUmJdsXXGlY0hnwA?e=JaGru3Il materiale è stato testato con Ubuntu 20.04 con architettura x86_64. Non dovrebbero esserci problemi con altre release. Per iscriverti al workshop del 25 settembre, segui le pagine social di Cyber Saiyan (organizzazione di Romhack) Linkedin: https://www.linkedin.com/company/cyber-saiyan/ Twitter: https://twitter.com/cybersaiyanIT Link all’evento: https://romhack.camp/camp-schedule/ Inoltre, per rimanere […]
Slide: https://hacktivesecurity-my.sharepoint.com/:b:/p/alessandro/EX9sSrCCRIlLqvkHoRl7_jQBB6xKgV_qLL9UA5fIwf2Cbw?e=cCQpixMateriale utilizzato nel video (per poter replicare i lab): https://hacktivesecurity-my.sharepoint.com/:u:/p/alessandro/EX08cV3wTzZJsEeEQwZvw80BbybF2CpUmJdsXXGlY0hnwA?e=JaGru3Il materiale è stato testato con Ubuntu 20.04 con architettura x86_64. Non dovrebbero esserci problemi con altre release. Per iscriverti al workshop del 25 settembre, segui le pagine social di Cyber Saiyan (organizzazione di Romhack) Linkedin: https://www.linkedin.com/company/cyber-saiyan/ Twitter: https://twitter.com/cybersaiyanIT Link all’evento: https://romhack.camp/camp-schedule/ Inoltre, per rimanere […]
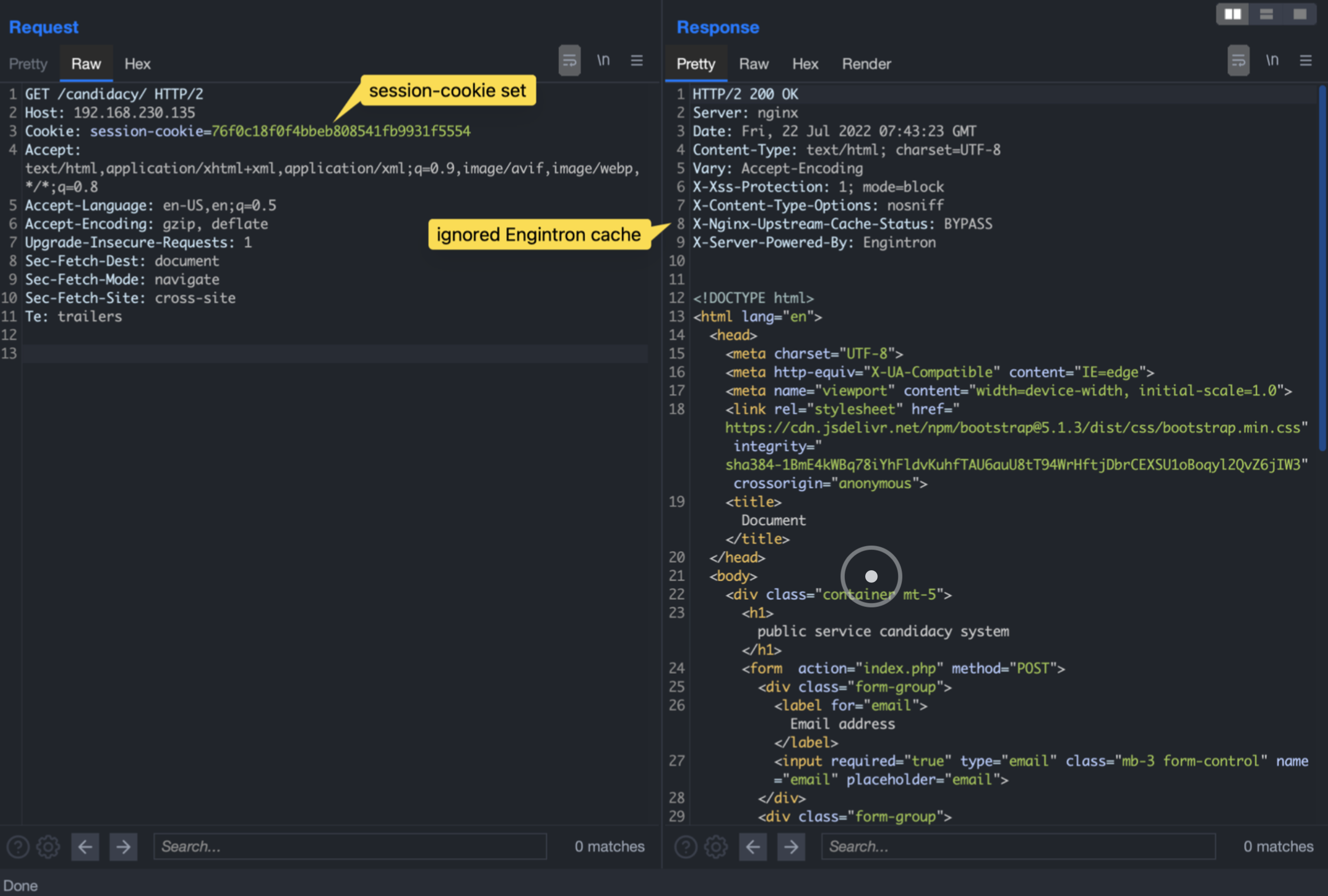
Tl;DrThe Engintron plugin for CPanel presents a default configuration which could expose applications to account takeover and / or sensitive data exposure due to cache poisoning attacks. Whenever a client sends a request to a web server, the received response is processed and served by the back-end service each time. In case of an high […]
Introduction I was searching for a vulnerability that permitted me to practise what I’ve learned in the last period on Linux Kernel Exploitation with a “real-life” scenario. Since I had a week to dedicate my time in Hacktive Security to deepen a specific argument, I decided to search for a public vulnerability without a public […]
Introduction Github project: https://github.com/kiks7/KRWX During the last few months/year I was studying and approaching the Kernel Exploitation subject and during this journey I developed few tools that assissted me (and currently assist) on better understanding specific topics. Today I want to release my favourine one: KRWX (Kernel Read Write Execute). It is a simple LKM […]