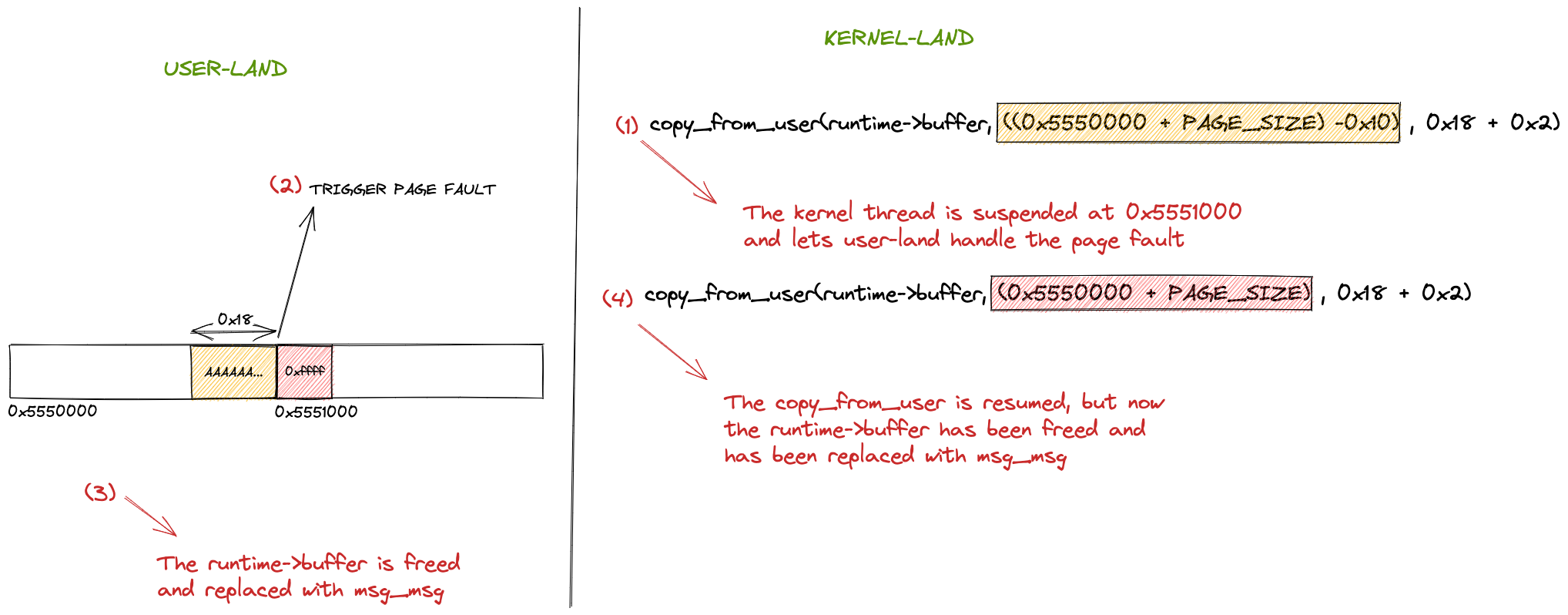
Introduction I was searching for a vulnerability that permitted me to practise what I’ve learned in the last period on Linux Kernel Exploitation with a “real-life” scenario. Since I had a week to dedicate my time in Hacktive Security to deepen a specific argument, I decided to search for a public vulnerability without a public […]
- info@hacktivesecurity.com
- Mon - Fri: 9.00 am - 6.00 pm
Advanced Security Solutions to protect the Cyberspace.