Introduction In the previous blog post, we have dissected the Lorex 2K IP Camera from an hardware perspective. The main objectives were to obtain an an interactive shell and extract the firmware for further analysis. Although the first point was not achieved due to the target hardening, we were able to extract the firmware. Since we also had […]
Introduction Not all stories end with the expected and hoped-for results, and this story is one of them. We’re releasing a three-part series detailing our unsuccessful Pwn2Own 2024 attempt targeting two IP cameras. The contest forces you into a completely different mindset compared to standard security assessment activities. Here, you have only one objective: compromise […]
Introduction This blog post is about a manually Reverse Engineered challenge we have written for this year NoHat24 security conference. The conference was a blast and we also did our best to contribute also with a worskhop on Linux Kernel Fuzzing. The challenge is a compiled C/C++ binary that implements a custom TCP protocol that […]
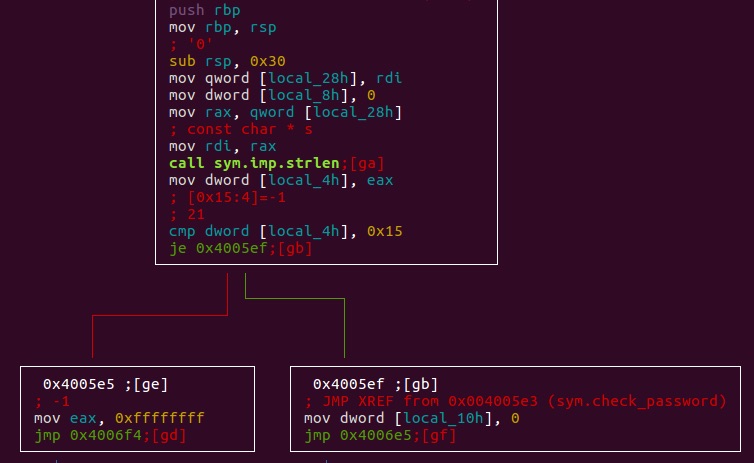
I don’t usually play CTFs, but this time i wanted to improve my radare2 and reversing skills.All crackme challanges can be found here.Levels from 1 to 3 are really entry-level, from 4 ahead start to be interesting. As the README says: “It’s reverse engineering, not cracking.”. That means we don’t have to patch the binary in […]