On March 13th, by using dnsrecon (https://github.com/darkoperator/dnsrecon) and a huge wordlist, I came across with an Amazon domain (hireon.amazon.com) with a Reflected XSS.
Usually I don’t use to write an article for an XSS vulnerability, but I would share a trick I discovered during this analysis.
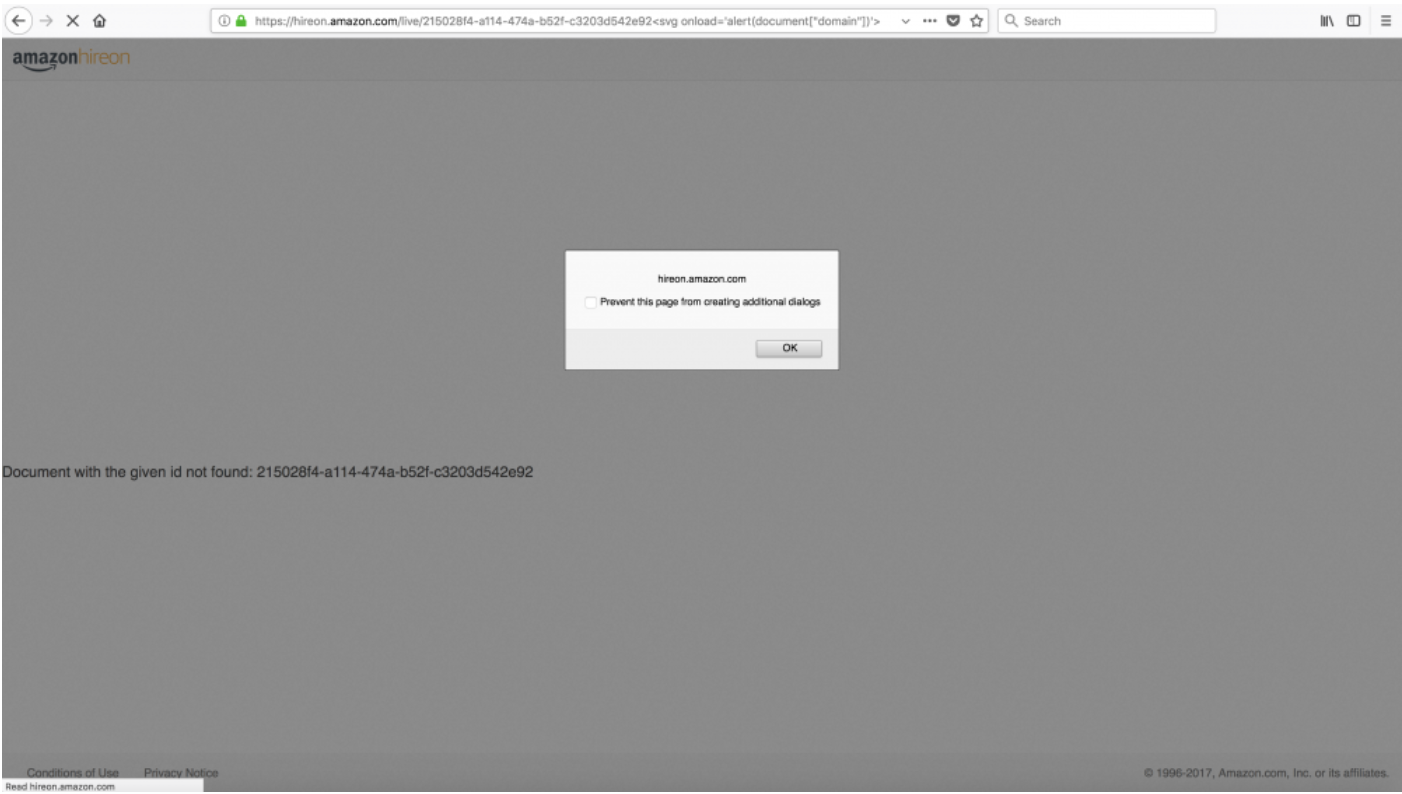
Looking for a not existent resource, the following error message was displayed on the web page.
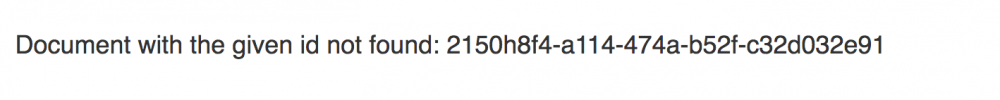
If a string was concatenated to the resource id, then it was printed on the page. At the first stage I tried to use html tags and no input validation was performed at all. Then I tried to use javascript code and I have found a couple of filters for some special characters. In particular when the “dot” (.) character was detected an error message was thrown.
In order to show an alert box with the current domain name (or cookies) I should have used “document.domain” or “document.cookie” but because of dot character I had to find an alternative way. At that point I tried to use the document object like an associative array (as shown in the following screenshot) and I was able to show the current domain name within the alert box.
document[“domain”] or document[“cookie”]
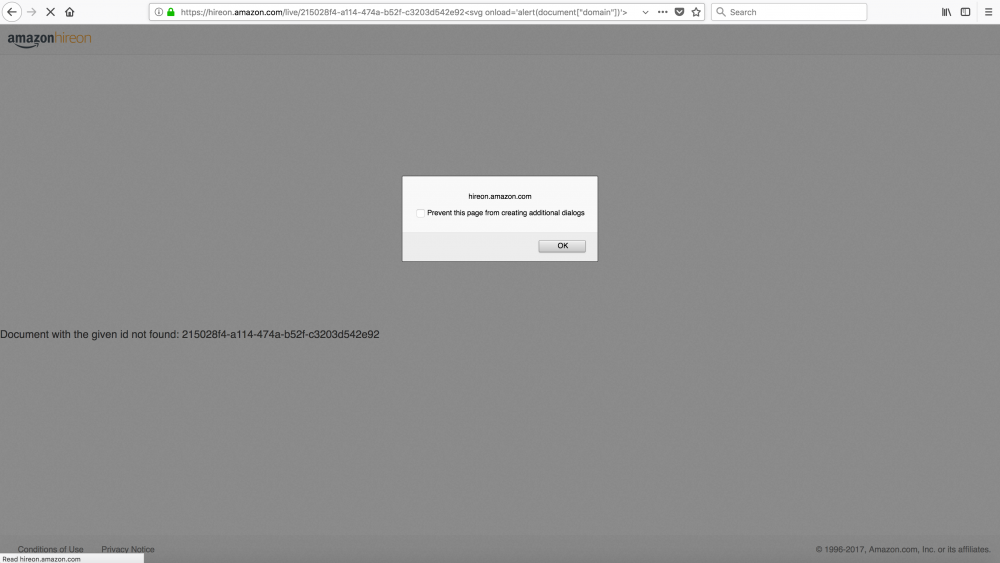
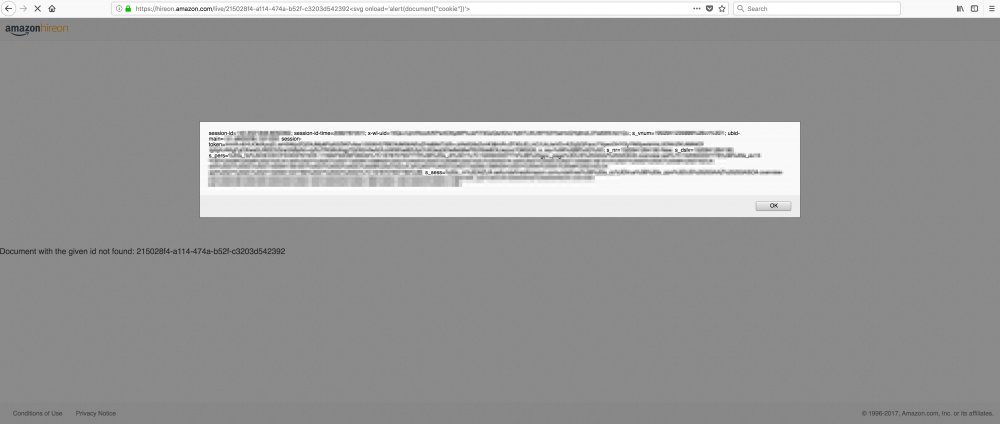
On March 21st, Amazon changed the domain name in livecode.amazon.jobs but the XSS was still there.
Finally, on March 26th, the XSS was completely fixed.
Timeline
– March 13th – First contact
– March 21st – Domain change but the vulnerability is still there.
– March 26th – Fixed
(Carlo Pelliccioni)
Recent Comments