During our research activities we discovered an authenticated local inclusion in the Simple Job Board WordPress plugin.
The Simple Job Board WordPress plugin has reached over 20,000 active installations and an excellent reputation in terms of reviews, allowing the simple and efficient management of job offers.[1]
Directory traversal allows an attacker to step out of the root directory and have an access to other parts of the file system. This might give the attacker the ability to view restricted files, which could provide the attacker with more information about the operating system and source code itself (download source code files).
Tested on:
– v2.9.3 (latest)
– v2.8.82 – PHP 7.2.21
Working on version > 2.4.3
Authenticated Directory Traversal
The Simple Job Board plugin allows to receive a candidate’s resume for a job offer.
To Each candidate is assigned an application number and the resume is made accessible to an HR user through the following link
https://localhost/wp-admin/post.php?post=application_id&action=edit&resume=application_id
Or with the paid component `Multiple Attachment Fields Add on`[2]
https://localhost/wp-admin/post.php?post=application_id&action=edit&sjb_file=application_id_filename.pdf
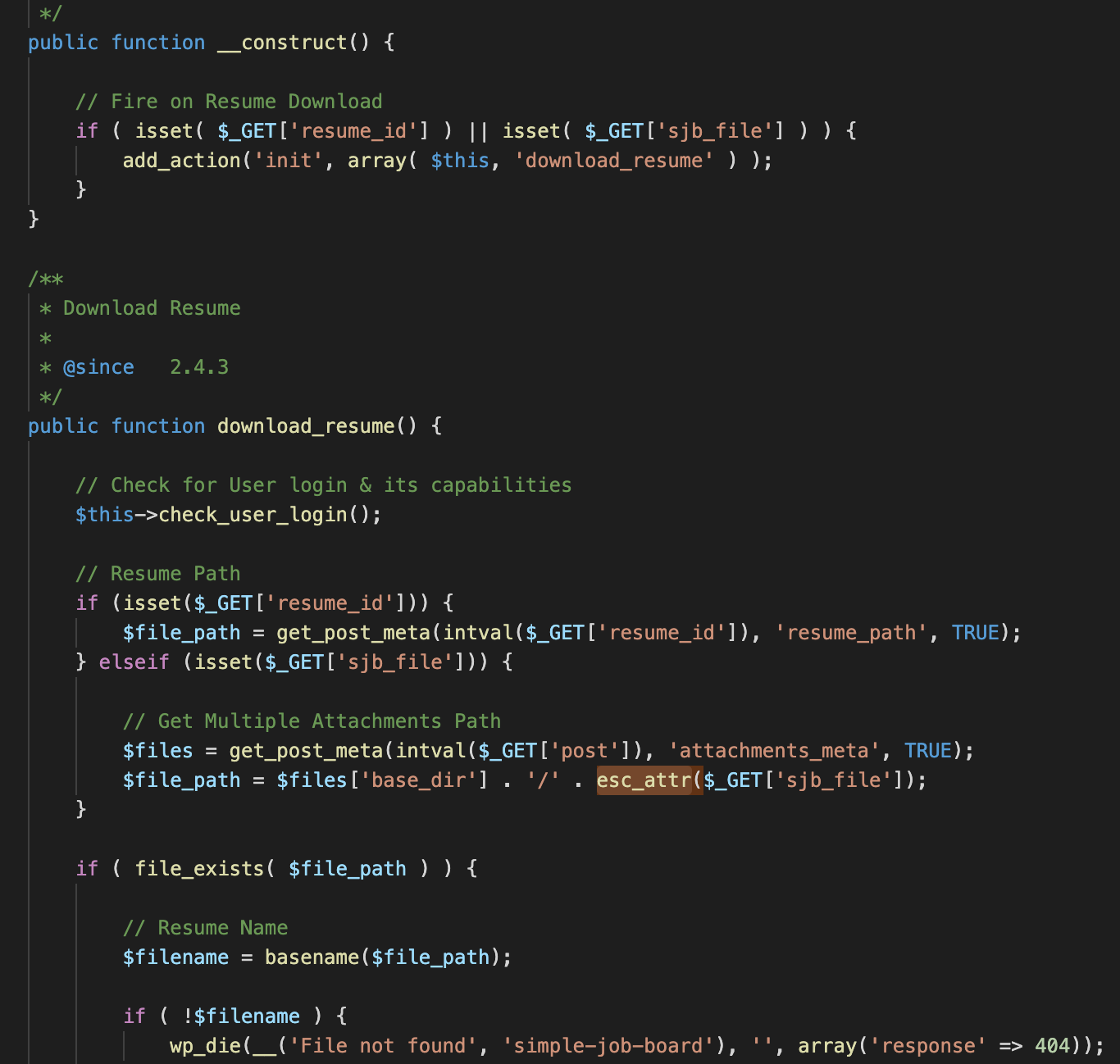
Looking for some references of the parameter in the code, we found that the
File : simple-job-board/includes/class-simple_job_board_resume_download_handler.php
Following the field $_GET[‘sjb_file’] it is never sanitized, the esc_attr() function execute only an html encoding [3].
So the $filepath variable at the end contains
$files[‘basedir] (‘/var/www/html/wp-content/uploads/jobpost/2020’) and
$_GET[‘sjb_file’] (filename)
After the basename check an header(‘Location ’.$filepath) is executed, so we can exploit this.
The upload location for the resume is :
`/wp-content/uploads/jobpost/2020/application_id_resume.pdf`
So the following link show how the directory traversal can be exploited going back to the folders:
https://localhost/wp-admin/post.php?post=application_id&action=edit&sjb_file=../../../../wp-config.php
[1] https://wordpress.org/plugins/simple-job-board/
[2] https://market.presstigers.com/product/multiple-attachment-fields-add-on/
[3] https://developer.wordpress.org/reference/functions/esc_attr/
Recent Comments