During a security assessment, we found an Insecure Direct Object Reference on Prestashop. In particular, the finding could allow an attacker to leak personal information such as first name, last name, phone number, shipping and invoice address.
This vulnerability affects all versions before v1.7.6.0 RC2 and was referred as BUG FIX #14444 in the Changelog. (changelog_1.7.6.0-rc2.txt)
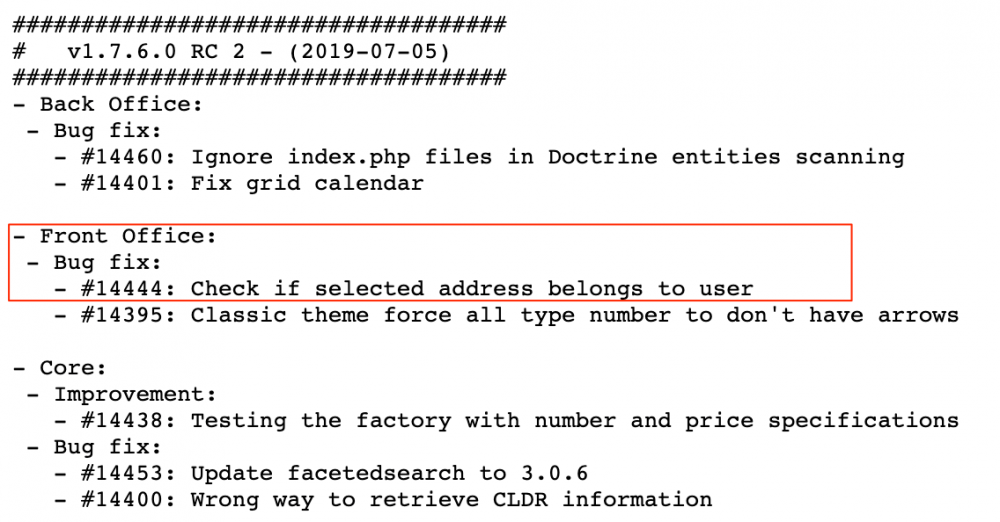
The vulnerability resides in the checkout process, during the selection of the delivery and invoice addresses. These addresses are bound to a global incremental ID and are sent without checking that the relative ID belongs to the current user. This could lead to an information leak affecting customers data.
As previously mentioned, all the versions <= 1.7.6.0 RC2 are affected but the payload is not the same for all of them. On older versions (such as v1.6.1.17) addresses can be leaked in the second stage of the checkout process if the “final summary” option is enabled (this option shows delivery and invoice address) before the payment.
In the latest version, in order to leak other personal information the whole checkout process must be completed and then the leaked information will be shown in the orders history.
Timeline:
01/07/2019 : First contact with the Vendor
01/07/2019 : Acknowledge from the vendor
05/07/2019 : Patch released
09/07/2019 : CVE-2019-13461
(Alessandro Groppo)

Recent Comments