The devil and holy water
THE SITUATION
Having had the opportunity to observe a few hundred companies over the past 30 years, to date there is a greater and growing awareness of information security issues or corporate security more generally. It can be said that a good portion of the corporate and medium-sized enterprise has become well aware of the topic, in several cases somehow forced…
However, “pockets of resistance” still exist. There are still too many occasions, despite we are in 2023, when we find entities employing thought, energy and thus resources in comparing the “minimalistic approach” to security, when not merely cosmetic, of some corporate departments (the holy water), and the systematic, functional and substantial approach suggested by corporate security departments (the devil), whether or not headed by Chief Information Security Officers, Security Managers, or their equivalents. Still a bipolarity that tends to place the parties in constant confrontation, procrastinating investments and thus risk mitigation actions, a condition that is based on a continuous ideological clash, further fuelled by the pattern of prevarication typical of classic vertical hierarchies.
Finally, it should be reminded that investments in security can no longer be promoted and/or tied solely to the sensitivities of willing individuals (often considered a nuisance), since by current legislation, industry regulations and in addition to the standards that permeate the marketplace, common security measures and controls for the protection of information (and people) are on many occasions of mandatory adoption. I am not going to expand on listing these European and domestic, cross-cutting or industry regulations and standards; many of you know very well which ones I am referring to.
QUESTION OF BALANCING FORCES
To better express the central concept of this article, we intend to use the principle of magnetism. A magnet has two poles: a positive force, here likened to optimism, i.e. the consideration that there is a low likelihood of an adverse event occurring that would affect normal business operations; the other pole, a negative force, pessimism, for the matter at hand is closer to realism, that is the expectation that risk mitigation measures will be put in place to produce an environment prepared to withstand the impact of any adverse events.
Having made this introduction, it can be said that corporate management by definition has an optimistic attitude, “natural optimism,” particularly toward the business, but also toward the likelihood of risks occurring and consequently also toward the posture that the company should take on security.
In contrast, corporate security can only assume, by nature, a pessimistic attitude, “natural pessimism,” regarding the likelihood that risks may occur. This is normal, otherwise in the presence of excessive optimism a security department would produce a paradox and would certainly be of no use.
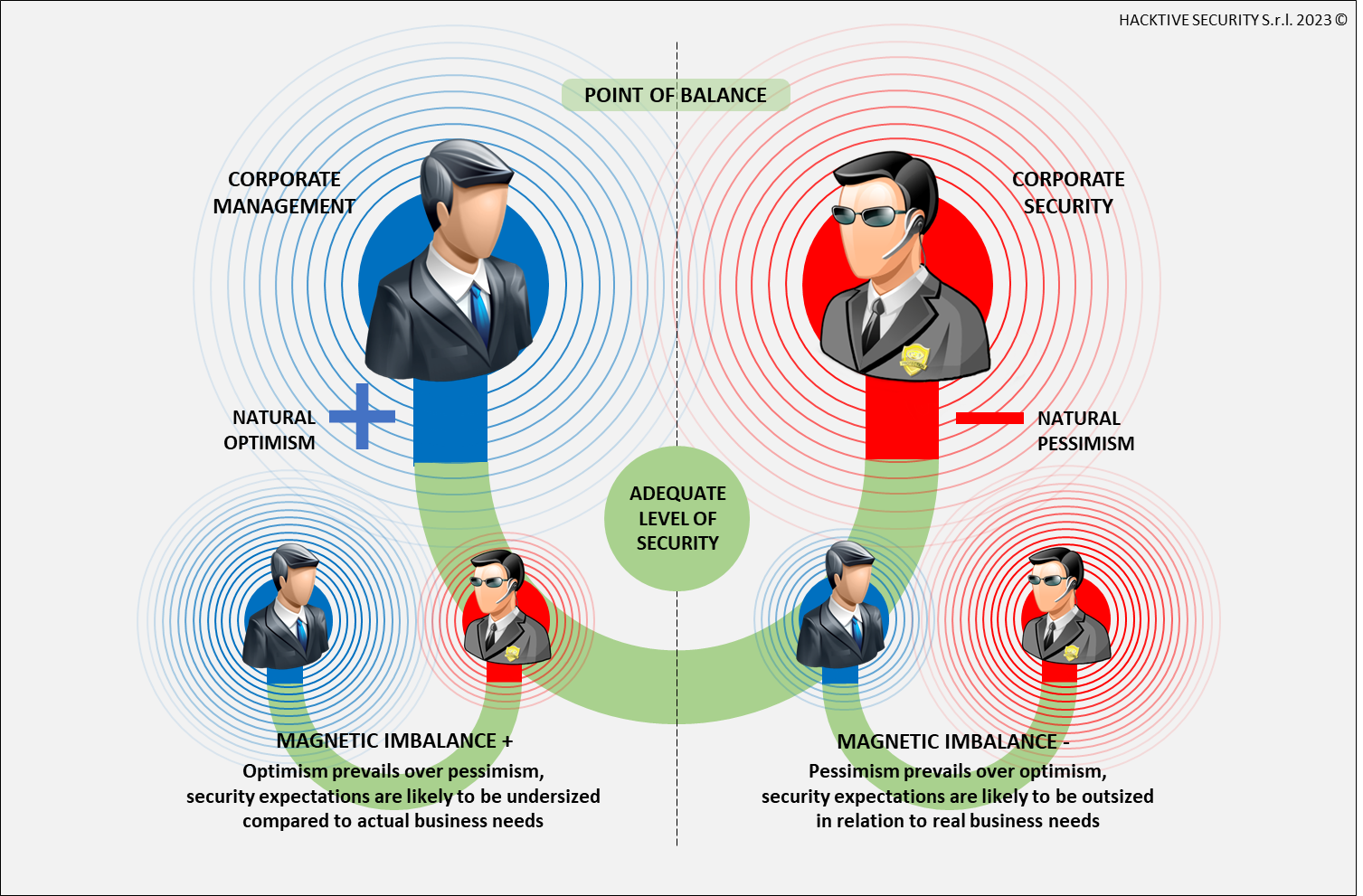
Figure 1: the balance point
Thus, reaching a “balance point” between the parties leads to the consideration that there is precisely a proper relationship and balance between optimism and pessimism, such that an appropriate security posture can be pursued and achieved, implemented through proper risk evaluation and treatment, within a shared cost-benefit ratio.
However, in the absence of systematic risk evaluation, the approach may be more humoral and less objective. The imbalance caused by a preponderance of optimism (and sometimes wait-and-see attitude), can easily result in taking a security posture that is undersized compared to the critical issues present, to the real business needs, which manifests itself in disinvestment toward security processes. Similarly, the preponderance of pessimism, can lead to having security expectations that are out of proportion to the risk present and the needs of the company, leading to unwarranted investment and limiting the company’s flexibility.
In essence, an appropriate security posture is achievable through reaching a “balance point” between the opposing forces, achieving the correct balance between opposition to change (conservative spirit) and the needs for innovation (progressive spirit).
PREJUDICIAL FACTORS
Some of the main pre-conditions that play against reaching the “balance point” can be summarized as follows:
- Inappropriate hierarchies: corporate security must be able to interact constantly, transparently and directly with the company’s management, in the absence of intermediaries who cause conflicts of interest and may jeopardize the achievement of the coveted balance. For example, a Security Office (or Security Manager) who reports and answers hierarchically to the IT Manager or Human Resources has very little room for manoeuvre, reduced ability to significantly influence the improvement of corporate security posture and almost certainly unable to develop the balance discussed above. Typical phrases and/or alibis: “security is an IT manager’s problem”; “we are not sufficiently structured to operate differently”; “the management cannot also deal with the security issues”; “we are not NASA”, etc.;
- Deficiencies in security culture: or the very real absence of a security culture, which in most cases needs bottom-up actions to empower the entire corporate population. Typical phrases and/or alibis: “we are just a bank, we are not a government intelligence department”; “security is taken care of by the external consultant”; “don’t waste staff time with security”, etc.;
- Lack of periodic disclosures: the best way to consolidate the absence of interaction with corporate management and undermine the spread of security culture is to fail to provide senior management with periodic reports on the progress of security processes, the critical issues present and, above all, regarding the benefits and objectives achieved, as well as the tenor of return on investments made. Typical phrases and/or alibis: “management is not interested in understanding security risks”; “the management only gives us 30 minutes of its time”; “we cannot involve management in security information events”; etc.;
- Lack of commitment: to a lesser extent inappropriate hierarchical relationships, to a greater extent deficiencies in the security culture of top management, are factors that tend to hinder the likelihood that security initiatives and/or projects will be promoted at all levels of the company by top management. Typical phrases and/or alibis: “we’ve always done it this way”; “let’s do the bare minimum, preferably ‘just fronting'”; “don’t make us spend money, security is just a cost to the company”; “security is only about enterprise IT issues”, etc.;
- Excessive turnover: assigning insufficient resources, failing to provide for staff growth, and establishing a general unfavourable, frustrating and uncooperative climate do not contribute to the consolidation of corporate security, but rather incentivize systematic staff turnover that is embodied in a continuous swing in the security posture of the company, sometimes resulting in recession to initial and tragically critical conditions. Typical phrases and/or alibis: “if we train staff, they will leave the company”, “training is expensive and distracts staff from operations”; “training is only a cost to the company”; etc.;
- Lowering the bar: last point, but certainly not in terms of importance. Reducing the quality level of operations, particularly when talking about security, is counterproductive, dangerous and at the very least anachronistic. Preparation, quality and attention to detail make a difference and are key factors in creating the “balance point” and preparedness to withstand the impact of adverse events. In the typical division of the corporate population between “sad” and “cheerful”, great care must be taken not to be carried away by the “sad” into operational models that base their foundations on the continuous and inexcusable detriment of quality. Typical phrases and/or alibis: “the company is not yours”; “it is urgent”; “we have to do it quickly”; “can you turn a blind eye to this aspect ?”; etc.
CONCLUSIONS
While it may be feared that the years ahead may be dominated by a certain tendency toward chaos (social chaos, media chaos, geopolitical chaos, financial chaos, etc.), there is a certain conviction that as far as relative to the successful enterprise, capable of competing transnationally, with particular reference to certain productive sectors (e.g., banking-insurance, financial, telecommunications, self-driving cars, etc. ), with the ability to govern and not be subjected to the sometimes worrying evolution of technologies, this must be a regulated and adequately secure enterprise, capable of effectively containing risks and providing sufficient guarantees to the parties involved (including consumers and staff) about its ability to subsist in the marketplace and effectively deal with the adverse events it may gradually face.



Recent Comments